Tags are a really useful component in VMware. They can be used for all manor of things, whether it’s for storage policies, backups, identifying a group of objects or in the case of this post, managing permissions.
Having a method of easily assigning permissions to singular or multiple objects in vCenter can be a great benefit to a vSphere Admin as it’s gives them greater control over the environment they manage.
Lets take a look at what is needed to get this setup:
- Script
- Tag Category & Tags for each support role.
- AD Security Groups
- AD Service Account
- vCenter Roles (one for the service account, then one for each of the support roles)
- PowerCLI VICredentials
- Scheduled Task
In this example I will use 4 common support teams that could be used, DBA, EUC, Operations and Storage. These can be anything you have a requirement for.
Script
Here is the script that applies the permissions based on the assigned tags. It can also be found here on GitHub. Save this on your management server of choice, or wherever you intend to run the scheduled task as a .PS1 file. In this example it’s saved on a management server in C:\Scripts\VI_Permissions.ps1.
1#Load PowerCLI Modules
2Import-module VMware.PowerCLI
3
4#Get the Credentials
5$creds = Get-VICredentialStoreItem -file C:\Scripts\VM_Tagging_Perms.creds
6
7#Connect to vCenter
8Connect-VIServer -Server $creds.host -User $creds.User -Password $creds.Password -Force
9
10#Tags
11$dbaT = "Support Team/DBA_Team"
12$storT = "Support Team/Storage_Team"
13$eucT = "Support Team/EUC_Team"
14$operT = "Support Team/Operations_Team"
15
16#Active Directory Groups
17$dbaG = "smt-lab\dba_admins"
18$storG ="smt-lab\storage_admins"
19$eucG = "smt-lab\euc_admins"
20$OperG = "smt-lab\operations_users"
21
22#Roles
23$dbaR = "DBA VM Administrator"
24$storR = "Storage VM Administrator"
25$eucR = "End User VM Administrator"
26$OperR = "Operations Users"
27
28$VMs = Get-VM
29
30ForEach ($VM in $VMs) {
31
32 $TAGS = Get-TagAssignment -Entity $VM | Select @{l='SupportTeam';e={('{0}/{1}' -f $_.tag.category, $_.tag.name)}}, Entity
33
34 If ($TAGS.SupportTeam -contains $dbaT) {New-VIPermission -Principal $dbaG -Role $dbaR -Entity $vm.name} Else {Get-VIPermission -Entity $vm.Name -Principal $dbaG | Remove-VIPermission -Confirm:$false}
35 If ($TAGS.SupportTeam -contains $storT) {New-VIPermission -Principal $storG -Role $storR -Entity $vm.Name} Else {Get-VIPermission -Entity $vm.Name -Principal $storG | Remove-VIPermission -Confirm:$false}
36 If ($TAGS.SupportTeam -contains $eucT) {New-VIPermission -Principal $eucG -Role $eucR -Entity $vm.Name} Else {Get-VIPermission -Entity $vm.Name -Principal $eucG | Remove-VIPermission -Confirm:$false}
37 If ($TAGS.SupportTeam -contains $operT) {New-VIPermission -Principal $OperG -Role $OperR -Entity $vm.Name} Else {Get-VIPermission -Entity $vm.Name -Principal $OperG | Remove-VIPermission -Confirm:$false}
38 }
Tag Category & Tags
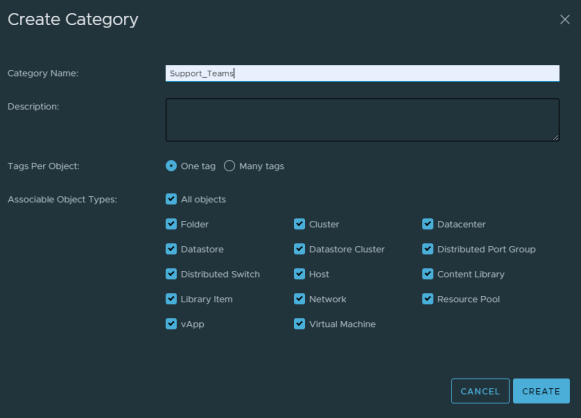
Now onto Tag Categories and Tags in vCenter. Create a Tag category called ‘Support_Teams’ (Or something of your choosing, just make sure you are consistent throughout):
Or using PowerShell - New-TagCategory -Name Support_Teams -Cardinality Multiple -EntityType All
You can select as many object types as you wish and you will also want to allow multiple tags per object.
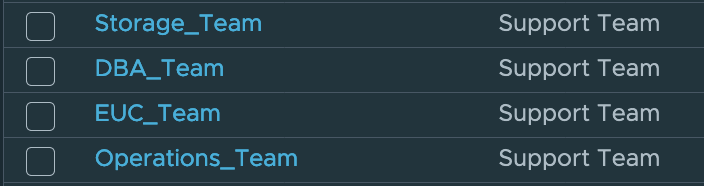
Now create a tag for each of the support teams in the tag category you just created:
1New-Tag -Name Storage_Team -Category "Support_Teams"
2New-Tag -Name DBA_Team -Category "Support_Teams"
3New-Tag -Name EUC_Team -Category "Support_Teams"
4New-Tag -Name Operations_Team -Category "Support_Teams"
Create AD groups
Now for some corresponding AD Security Group for each role you wish to have:
Service Account (AD User)
Now to create an AD user account that will be used to apply the permissions within vCenter. This will be the account that will be used to run the scheduled task, connect to vCenter and will have the appropriate permissions to assign permissions for the support roles.
Support Team Roles
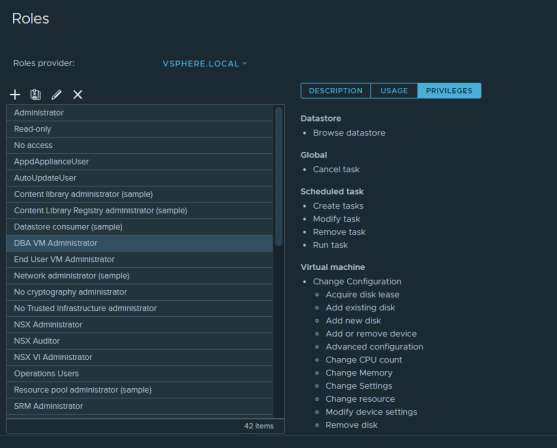
Now we need to create a suitable role for each team. In this example I have copied the Virtual Machine Power User role, but these roles can contain which ever privilege’s you require.
Under 'Administration > Roles' you will see the options to either create a new Role or copy an existing. From here you will be able to assign it a name and specify the privilege’s you require.
You will be referencing these Role names in the script so make sure you continue to match the names thought the process.
Permissioning Role
As mentioned in the service account section, the account (tag_permissions) running the scheduled task will need permissions in vCenter through a role. The privileges this role will hold, needs to include all the privilege’s that are referenced in all of your Support Team Roles in order for it to have the right to assign the permissions. For example, if all your support roles are a copy of the ‘Virtual Machine power user’ role, your tagging permissions role will need to contain the same privileges.
Depending on how broad the scope of your support team roles, you may want to use the ‘Administrator’ or the ‘No cryptography administrator’ role. This is entirely up to you and how you manage your estate.
For this example in my lab, I will use the predefined ‘Administrator’ role to grant the ’tag_permissions’ AD account permissions at the Global Root, ensuring you have selected the ‘Propagate to children’ option.
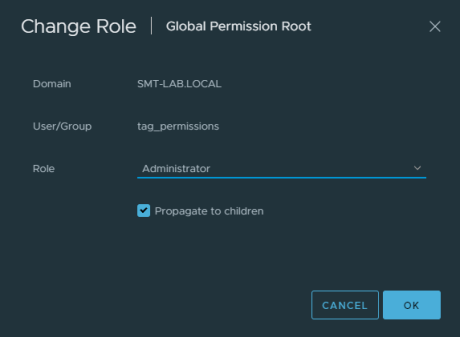
You could create a copy of the ‘Administrator’ role and name it something like ‘VI Permissions Service’ for instance, to give you flexibility to modify it in the future as well as making it easy to identify. With any high privileged account, ensure you secure it appropriately.
Create VI Credential Item
Now to create an encrypted credentials file that the service account running the scheduled task can import and then use to connect to vCenter without any intervention.
The AD account that is used to run the scheduled task, must be the account that also creates the credentials file as this is the only user that can use it. It will require permissions to run PowerShell and have access to a folder location to store the credentials file on your chosen management server.
To begin, start a PowerShell session in the context of the service account:
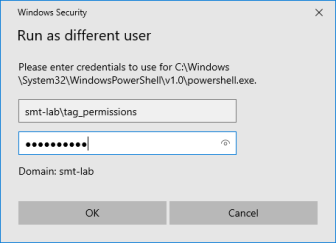
Note: Ensure the server that you are running this scheduled task from has PowerCLI installed. Installing PowerCLI.
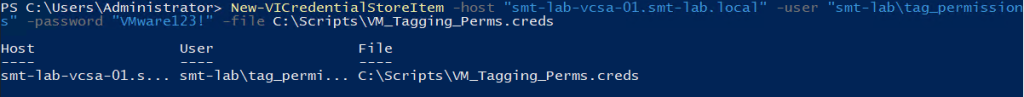
Then run the following, entering your vCenter FQDN and the user and password that you created:
1New-VICredentialStoreItem -host "smt-lab-vcsa-01.smt-lab.local" -user "smt-lab\tag_permissions" -password "VMware123!" -file C:\Scripts\VM_Tagging_Perms.creds
Ensure you are storing the file somewhere with appropriate access to allow this but, also to restrict any unnecessary access. The credentials file can have the password read if the user account that created it is compromised and gains access to the file using those windows credentials.
Scheduled Task
Now for the last component, the scheduled task. On a management server or a server of your choosing, create a scheduled task:
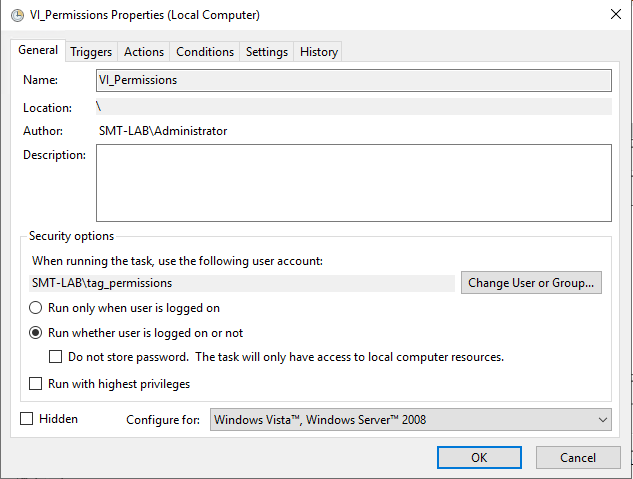
Assign an appropriate schedule that suits the level of change and size of your environment:
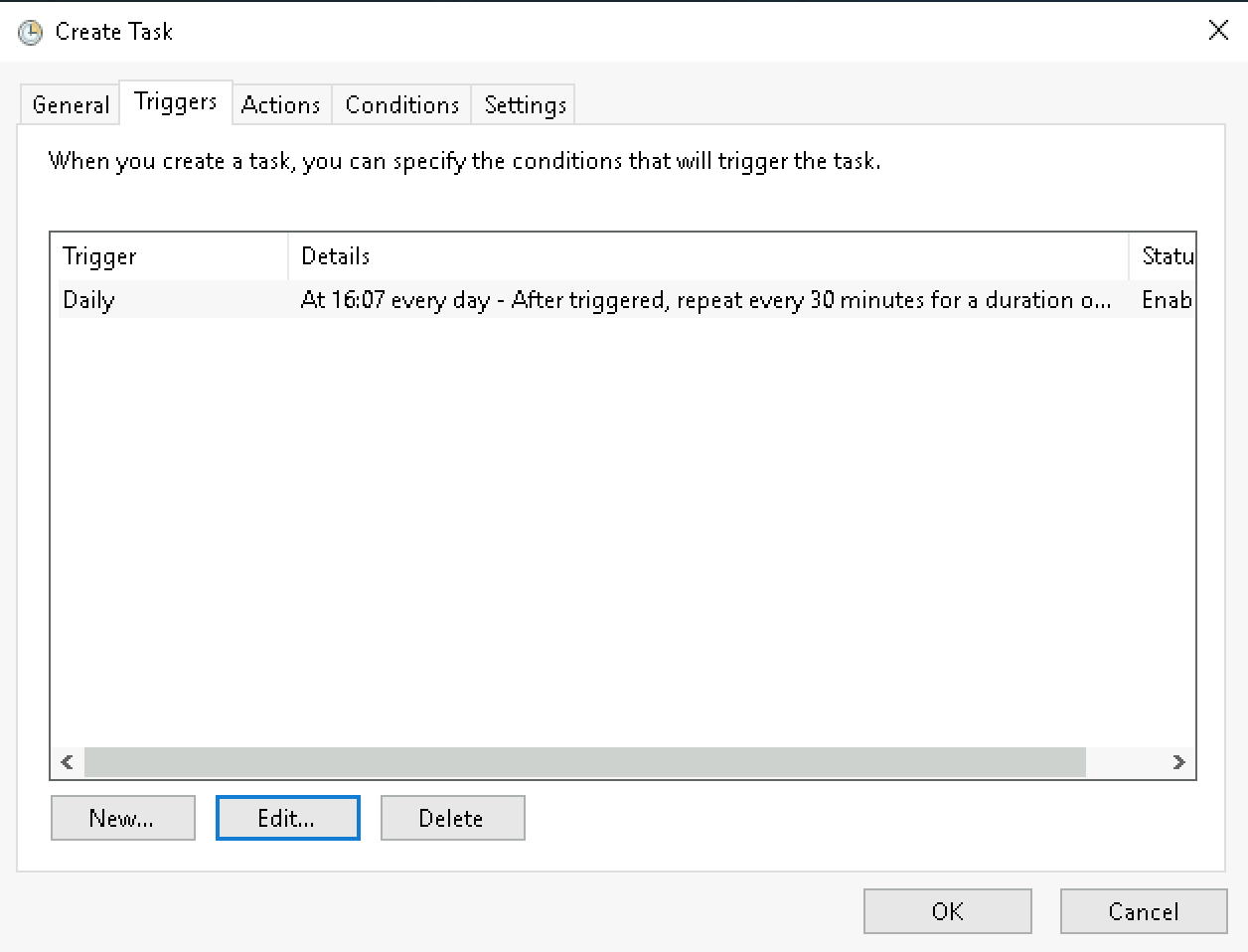
Now configure the trigger to execute the script:
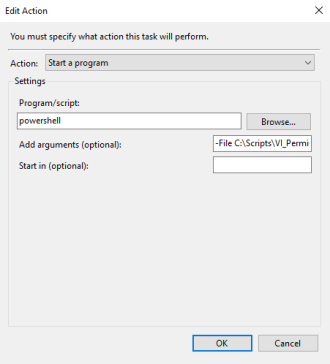
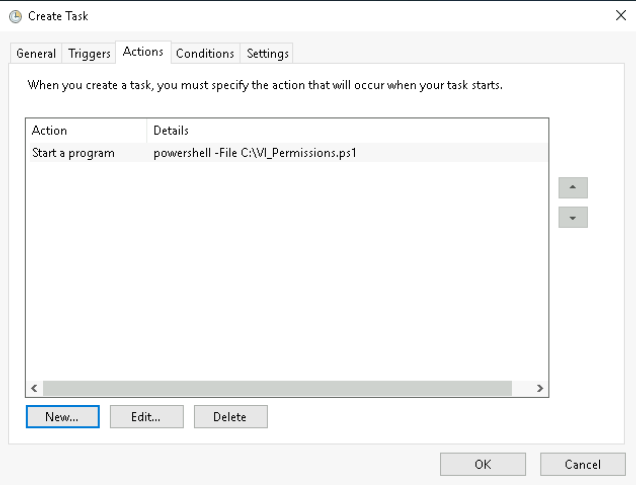
Now thats everything you need to set this up, so lets give it a run though!
Assigning Tags and Permissions
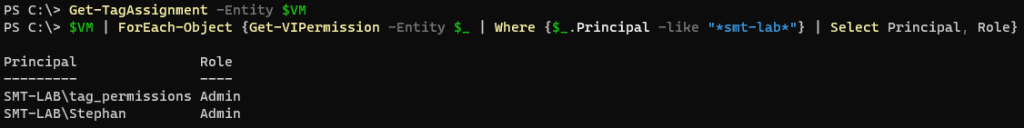
Lets take a look at my demo VM permissions before we begin assigning permissions:
Lets check the VM permissions before having any tags assigned:
1Get-TagAssignment -Entity $VM
2$VM | ForEach-Object {Get-VIPermission -Entity $_ | Where {$_.Principal -like "*smt-lab*"} | Select Principal, Role}
Note that the tag_permissions account has been propagated from the root permissions you set earlier.
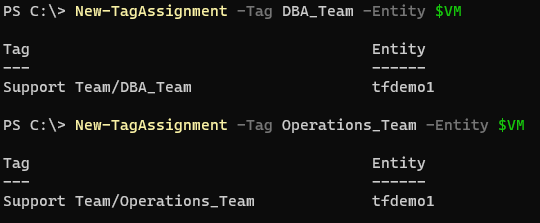
Now assign a tag or two from the ones you created earlier using ‘New-TagAssignment’:
1New-TagAssignment -Tag DBA_Team -Entity $VM
2New-TagAssignment -Tag Operations_Team -Entity $VM
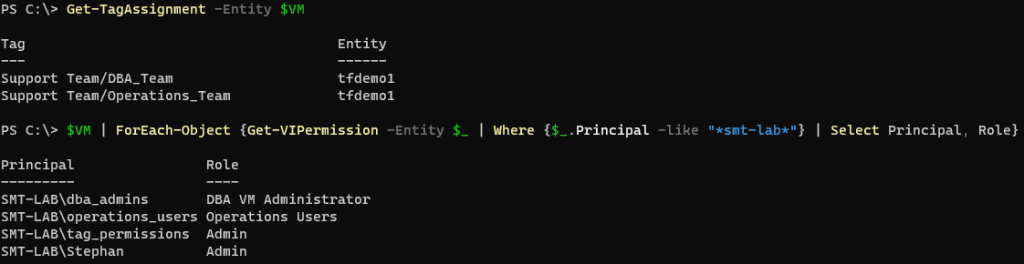
Now you can either manually run the scheduled task or wait until its next scheduled run time. Once the job has run, you can now check the tags match the permissions assigned by running the following:
1Get-TagAssignment -Entity $VM
2$VM | ForEach-Object {Get-VIPermission -Entity $_ | Where {$_.Principal -like "_smt-lab_"} | Select Principal, Role}
You will see that the two tags assigned align with the the two AD groups being granted the corresponding role.
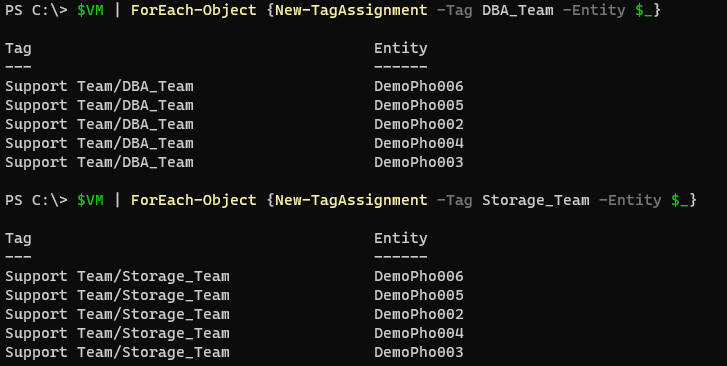
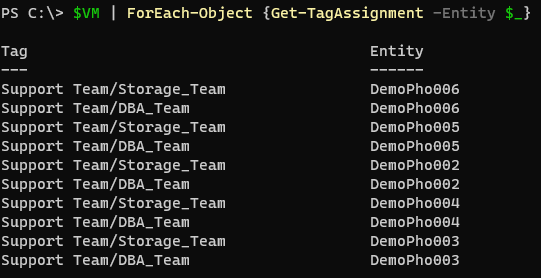
Now let do this for multiple VM’s:
Here I have multiple VM’s in the variable ‘$VM’ and I am assigning two tags to each of them.
1$VM | ForEach-Object {New-TagAssignment -Tag DBA_Team -Entity $_}
2$VM | ForEach-Object {New-TagAssignment -Tag Storage_Team -Entity $_}
You can now see the tags assigned:
1$VM | ForEach-Object {Get-TagAssignment -Entity $_}
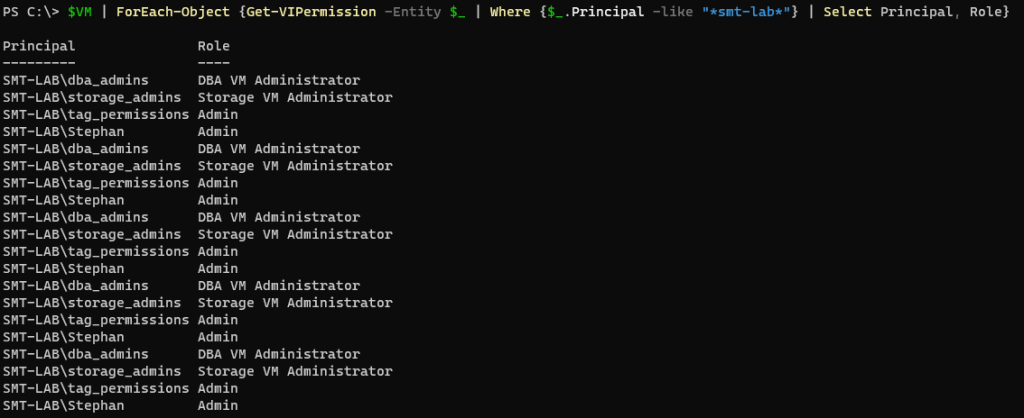
Following the script / job being run:
1 $VM | ForEach-Object {Get-VIPermission -Entity $_ | Where {$_.Principal -like "*smt-lab*"} | Select Principal, Role}
As in the singular example, you will see that the two tags assigned, align with the the two AD groups being granted the corresponding role.
Removing Tags and Permissions
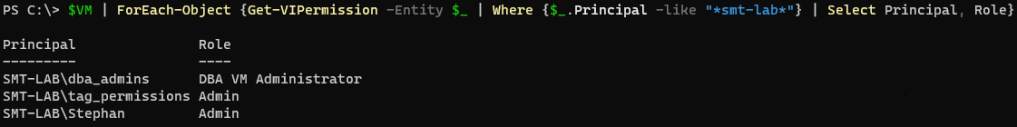
Now lets look at removing permissions, in this case, the Operations Team permissions from a VM:
1Get-TagAssignment -Entity $VM | Where {$_.Tag -like "*_Operations*_"} | Remove-TagAssignment -Confirm:$false
Leaving it with just the ‘DBA_Team’ Tag assigned:
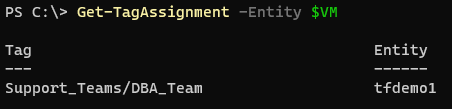
Once the script has run:
1$VM | ForEach-Object {Get-VIPermission -Entity $_ | Where {$_.Principal -like "*smt-lab*"} | Select Principal, Role}
Reviewing Permissions
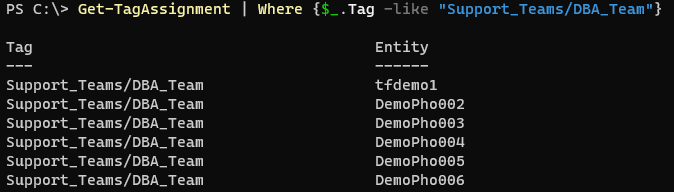
Finally, if you want to know which objects are supported by a specific team and have access you can check this by running:
1Get-TagAssignment | Where {$_.Tag -like "Support_Teams/DBA_Team"}
You now have a way of assigning and removing permissions from vCenter objects using Tags. In this example I have used virtual machine object, but depending on your requirements, and the scope you set on the tag category, you could use this for other vCenter objects.
Thanks for reading!