Is it secure?
This has to be one of the first things you consider with any technology solution or decision today. So when I was lucky enough to receive a NFR license from HyTrust for their KeyControl Key Management System I was excited to get this into my lab so I can make use of VMware’s vSAN and VM Encryption.
In this post I will be going through the process of deploying a HyTrust Key Control appliance and creating a trust with vCenter. It was surprisingly straight forward and I was up and running in no time at all!
Firstly, deploy the OVA to an ESXi Host or Cluster that isn’t going to be managed by the Key Control appliance. You don’t want your encryption keys in the same place as the objects you are encrypting!
Follow the OVF deployment wizard, providing the details as prompted, and once the appliance is online, complete the final configuration steps to finish the installation.
You will then be met with this screen -
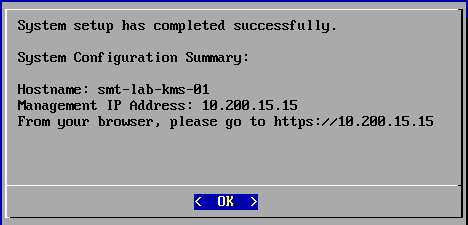
Now, browse to the web GUI and log in using the default credentials. You will then be prompted to set your own, followed by SMTP and online monitoring configuration options.
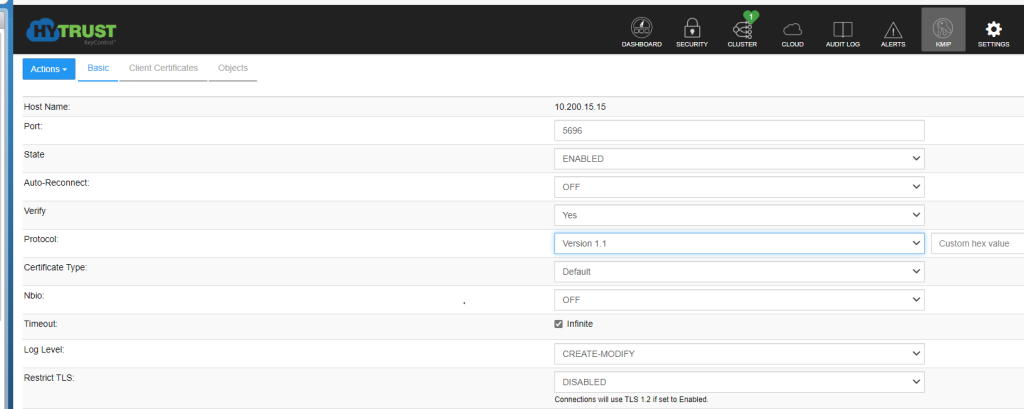
Once this is done and you are logged in there are a few KMIP settings you need to adjust in order for it to be ready to connect to vCenter as a Key Provider -
1State = ENABLED
1Protocol = Version 1.1
Below is a link to a HyTrust document with the details for vSphere 6.5. I used this for deployment in my vSphere 7 environment. You can find it here.
You will also want to apply a license file. This is done via; 'Settings > License', by way of uploading the license file you have been issued.
This completes a basic configuration that is now ready to connect to vCenter. If you are deploying outside of a lab environment, you are going to want to review your installation appropriately for the environment it is intended for.
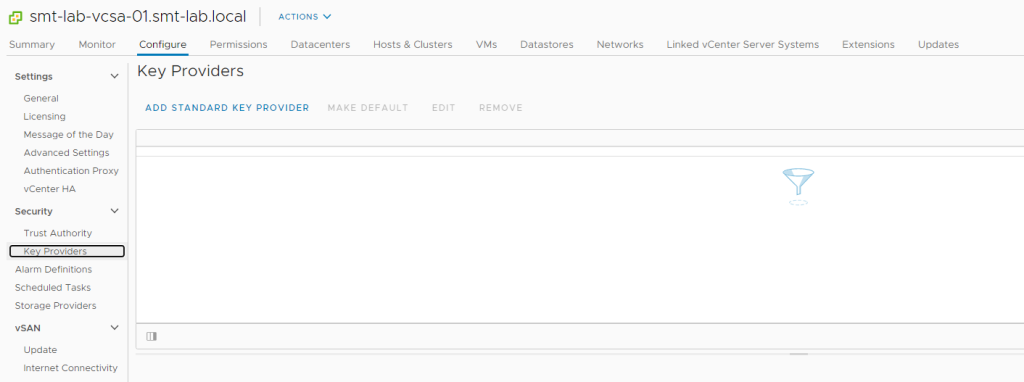
So over to the Web Client. Select the vCenter Server object, select 'Configure > Security > Key Providers' and hit ‘Add Standard Key Provider’.
You will then want to give it a name, followed by the requested information. Once done, click ‘Add Key Provider’
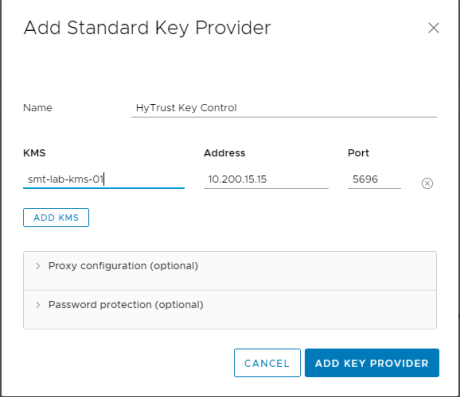
You will receive the following prompt to confirm you want to from the Key Provider you have entered. Click ‘Trust’
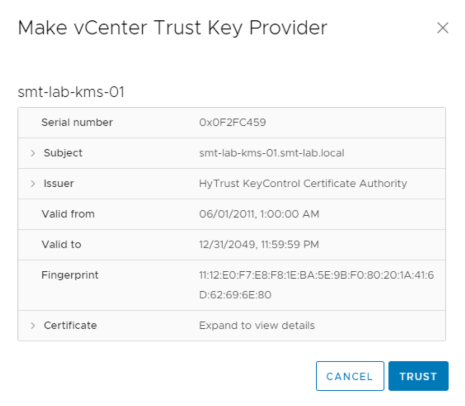
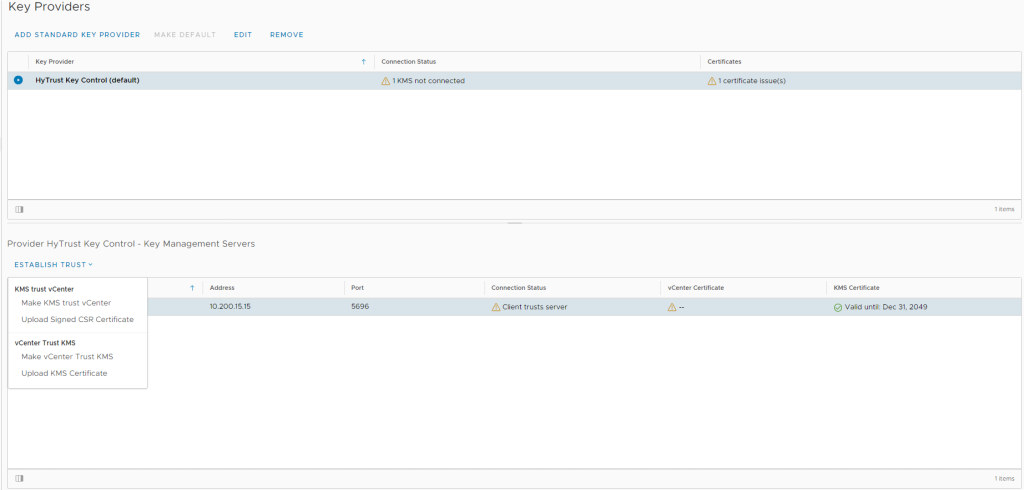
This will have now created a Key Provider, but will show that it is not connected and has a certificate issue. So next we need to set up the trust.
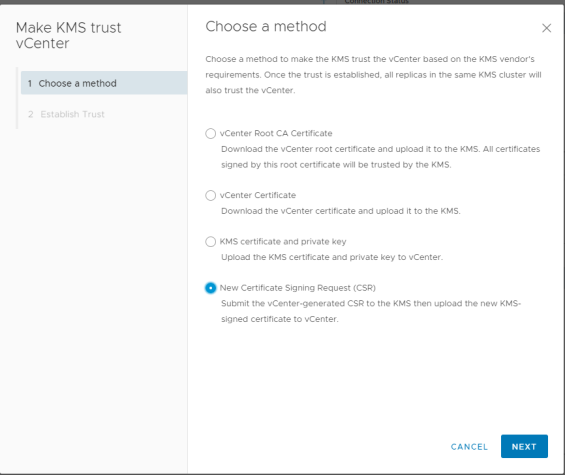
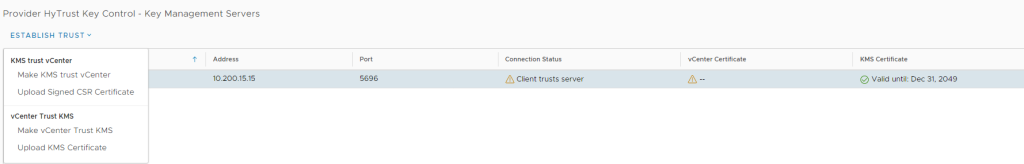
This can be done by clicking ‘Establish Trust’ and selecting ‘Make KMS trust vCenter’
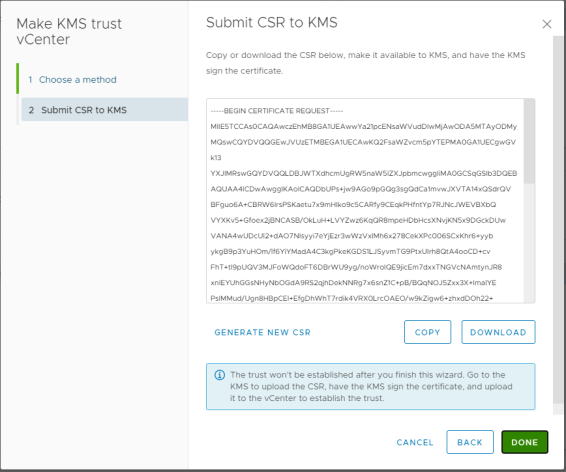
In my lab, I have gone with the option of creating a CSR and having the KMS issue a certificate -
Download the CSR using the option available. This will be in the .pem format which is exactly what you need.
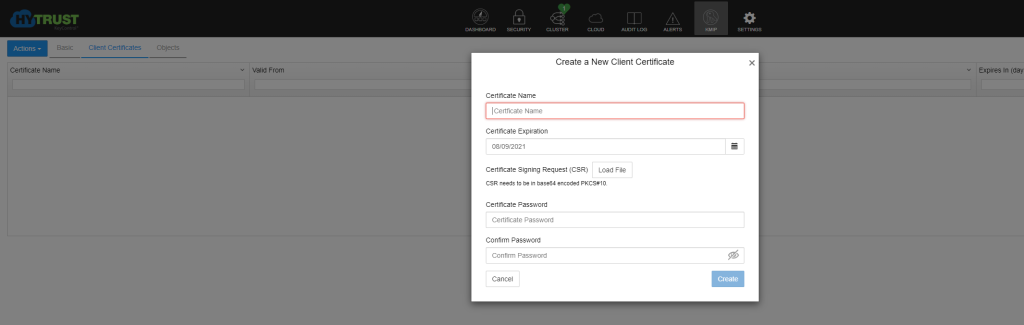
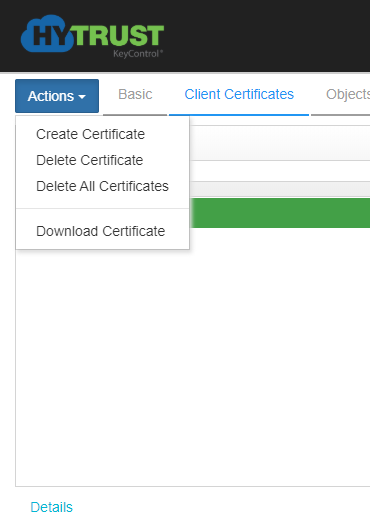
Now over to the HyTrust appliance, load the CSR we downloaded into the wizard, as well as a name, and hit create. This is via the KMIP menu and selecting ‘Actions’ followed by ‘Create New Client Certificate’.
Once this is done, select the certificate and click ‘Actions’ and select the ‘Download Certificate’ option. This again will come in the requested .pem format.
Back to vCenter, we now need to upload the certificate using the ‘Establish Trust’ option and selecting ‘Upload Signed CSR Certificate’.
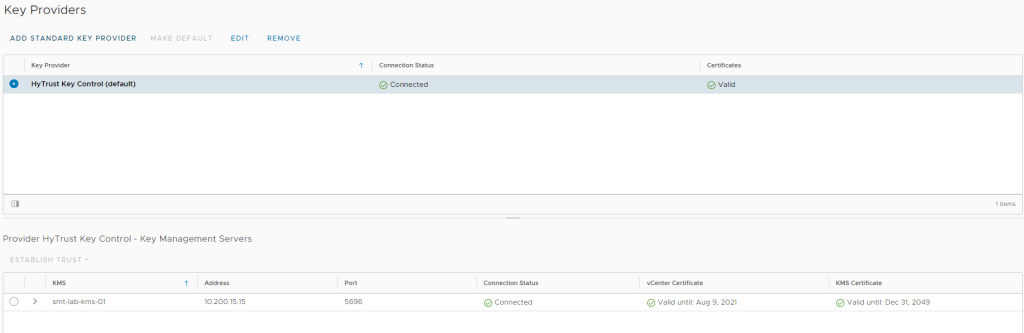
Once uploaded, you will see that the connection is now showing as connected and has a valid certificate.
This is now setup and ready to begin looking at VM and vSAN Encryption. Check out the next post which will go into both these options in more detail.
Thanks for reading.