In this day an age, securing data is a must. In this post I’d like to show you two options for protecting your data; vSAN Encryption & VM Encryption.
To achieve either of these you need to have connected a Key Management Server (or Cluster) to your vCenter server. Check out my previous post of how to do that - Deploying and Connecting a Key Management Server to vCenter.
Lets talk though VM Encryption first.
VM Encryption
VM Encryption is achieved using storage policies. By Default after configuring a KMS server, the ‘VM Encryption’ is available for use. Alternatively, you can create your own custom VM Encryption storage policy to include additional host based services such as caching and Storage I/O.
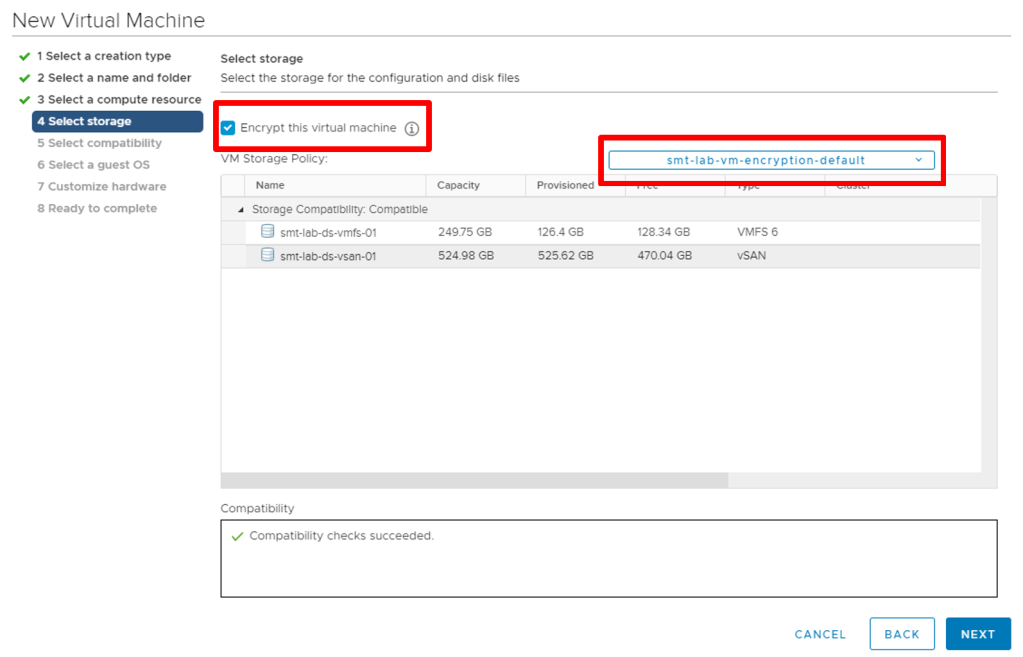
For a new VM, select the ‘Encrypt this virtual machine’ option on the ‘Select Storage’ section of the New Virtual Machine wizard. Then select the default encryption policy, or a custom one if you have one.
Then when customising your hardware you will see the following notification -
Once deployed, you will see confirmation of the virtual machines encryption status on the VM’s summary tab.
For an existing VM, it’s a slightly different approach.
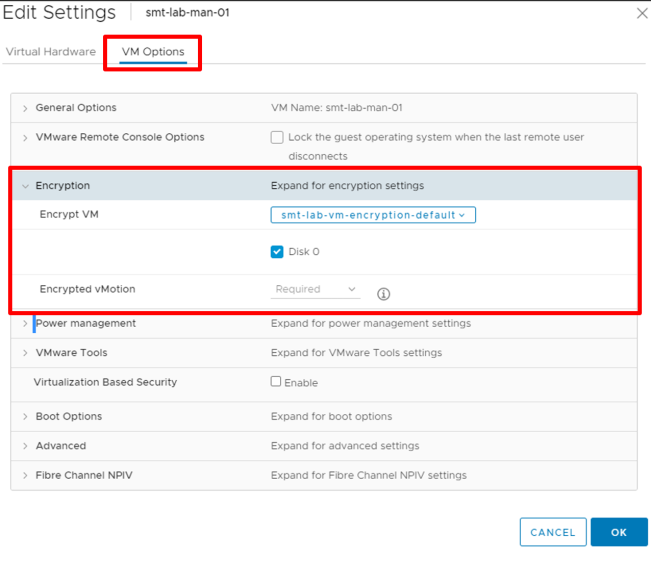
Firstly, power off the VM. Edit the VM’s settings and on the VM Options tab, expand the Encryption option and select your desired VM Encryption policy like so -
Below the policy you will see the option to select which disks you want to encrypt. In this test VM’s case, there is only one disk, disk 0. You can choose to only encrypt the VM and not the disks if you have a use case to do so. Disks you choose not to encrypt will have the datastore default policy applied to them.
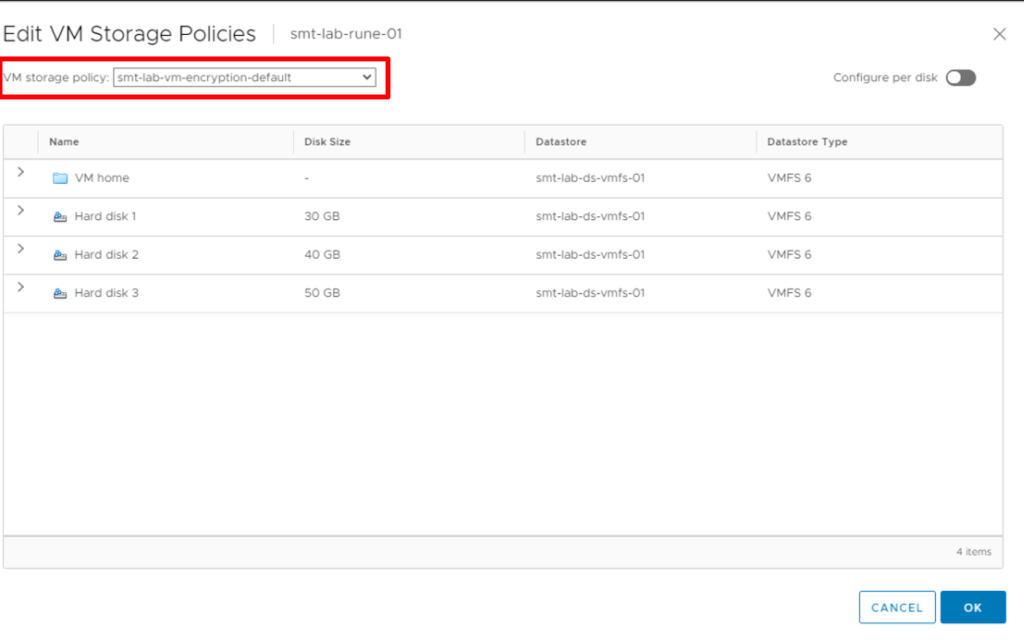
Alternatively, you can take a different route by editing the storage policy of a powered off VM to achieve the same result. Here you can also choose to ‘Configure per disk’. This is a useful option if you only have select hard disks you need to encrypt.
The VM will then reconfigure, this may take some time depending on the size of the disks, so make sure you factor this into your downtime window!
If you check out the performance backend monitor you will notice an increase in throughput an I/O while this is happening.
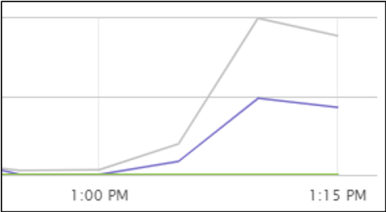
One disk at a time copies data from unencrypted to new encrypted disk. Once done, it attaches the new encrypted disk and deletes the old unencrypted disk. You will need enough disk space on the datastore to allow the duplication of the largest disk attached to the VM.
Once the task is complete, you will notice you have an updated encryption status.
Now the flip side, un-encrypting a VM.
This is a reverse of the process. Power off the VM, change the storage policy to a non Encryption policy and power back on when complete.
Now on to vSAN Encryption.
vSAN Encryption
To enable encryption for an entire vSAN cluster, its just a few clicks but there are a few things to be aware of.
- Make sure you have adequate free space within the vSAN cluster to allow for the rolling reformatting of the disk groups.
- There will be increased IO during this operation, make sure you choose an appropriate maintenance window to do this in so as to not cause unwanted impacts to your workloads.
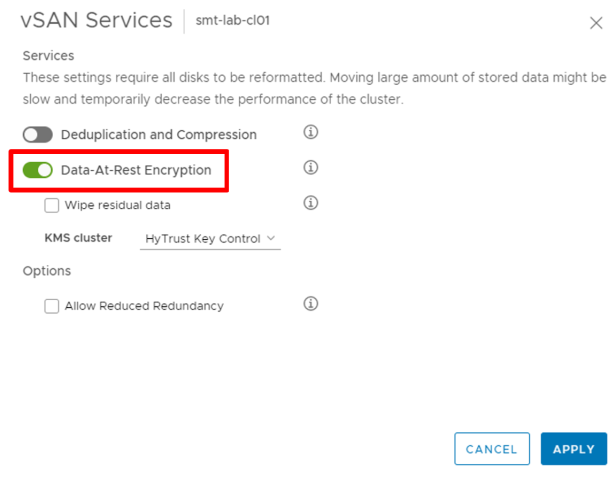
To enable this feature, select the cluster you wish to enable encryption on and browse to the ‘Configure > vSAN > Services option.
Click to enable ‘Data-At-Rest Encryption’.
You have the option to check the ‘Wipe residual data option’ if you have a need to. Bare in mind, wiping the storage can take a significant amount of time, so only use this option if you need to wipe existing data.
The final option is ‘Allow Reduced Redundancy’. This option will allow vSAN to run your workload at a reduced redundancy level during the encryption process. Make sure you understand the risks before using this option.
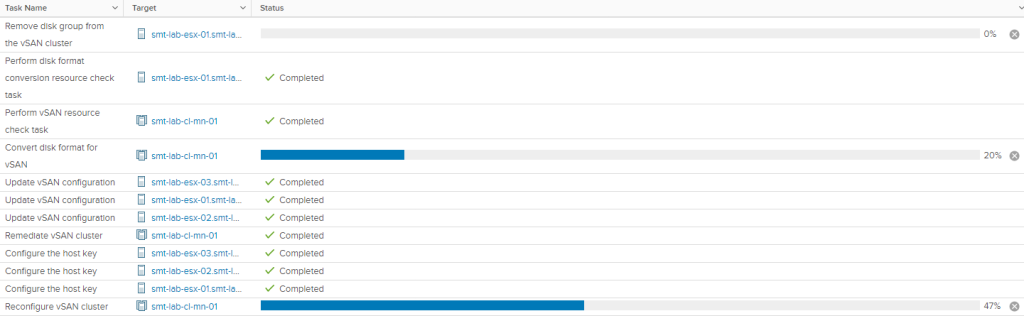
Hit apply and the cluster will begin reconfiguring.
Once it has cycled through each host in the cluster you will be able to see that the encryption status is now ‘Enabled’
Thanks for reading!